A typical cloud engagement has a dual responsibility model. There’s stuff that can be considered “below the line” and is the responsibility of the cloud service provider (CSP) and there’s stuff above the line, which is the responsibility of the customer.
Amazon have a good example for their IaaS:
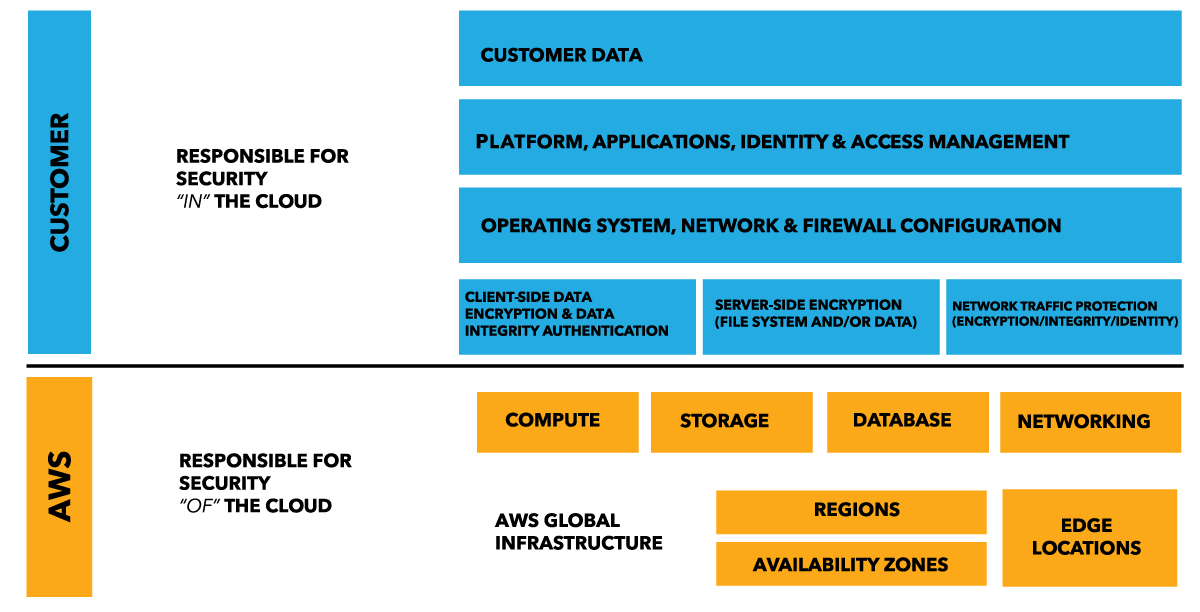
Where the line lives will depend on the type of engagement; the higher up the abstraction tree (IaaS->PaaS->SaaS) the more the CSP has responsibility.
But there’s a part of this that is frequently missed, and that’s the line itself. This line is typically where the CSP exposes controls to the customer (“self service” is part of the cloud model). For Amazon this may be the console where you can spin up a new VPC, new VMs, change firewall rules, modify VPC-VPC communication and so on.
This is clearly critical for a secure cloud offering. What use is there in defining a firewall if the console can be used to create a new VM with a connection to the internet and bypass this firewall?
We need to manage the management layer. Otherwise this layer can be used to bypass controls and create a shadow IT environment.
What this means will depend on your organisations stance and controls; is an audit and reporting control (detective) sufficient or do you want pro-active automated control over the management layer? Can your CSP provide the automation you need?
For an enterprise we may need to consider some questions:
- Who has access to this management layer (privileged access)
- Who has access to resources (end users)
- Who logged in?
- Who failed to login?
- What activities were performed
- What is the current configuration state
You’ll note these are the same sort of questions that an application control process would also ask; that’s not a surprise! We’re managing the cloud management layer the same as an app :-)
Some of these may be managed by Federation (can your existing authentication solution federate out of your datacenter?), or via synchronisation (hourly job that compares what users have permission to who should have permission), or (worst case) by a human eyeballing a screen.
Can your log infrastructure be reachable from the CSP (maybe a gateway service)? Can events be streamed into it, or pulled programmatically?
The breadth of the controls made available by the cloud service provider and how well we can integrate with them will impact the risk assessment of the cloud engagement; it is meaningless to have a locked down server inside an IaaS if we can disable all the controls through a weakly secured management plane!
